|
|
 |
The range of perspectives offered for how we understand “hacker ethics” including those from original open source activists like Raymond, definitions from Red Hat’s Linux Security Guide, and the more rigid guidelines found in the preparation manuals for becoming a “certified” ethical hacker make for a complex composite term. In short, these sources tell us that hacker ethics has everything to do with access, conduct, and motivation. Raymond’s contributions suggest that if a programmer wishes to be considered part of the hacker community, then he or she must endeavor to share work and keep access to code open. Access means more programmers can begin building and improving on another hacker’s progress without duplicating efforts. Within the hacker community, there is “the powerful sense that it is not merely inefficient but downright stupid, almost criminal, for people to have to solve the same problem twice” (Weber 138). Problems, even criminal ones, can come about when that access is assumed but not granted. The certified ethical hacker manuals instruct that nothing be hacked without permission. Conversely, Raymond contends that “system cracking for fun and exploration” falls into the realm of “ethically OK” as long as no harm is done. Meanwhile, the Red Hat security guide informs that any hacking without those permissions automatically classifies our conduct as “grey hat” hacking. So why hack? Raymond finds that motivation for our conduct is spurred by pure “intellectual curiosity” or the need for “circumventing limitations.” Hacking, according to Himanen, is most often “an activity that is intrinsically interesting, inspiring, and joyous” (6). Our perceived sense of satisfaction may come from contributing to solving a communal problem or it may “scratch a personal itch.” Of course, our desire to learn how something works or even improve on an existing program or web page does not automatically provide a legal justification for our conduct. Either way, designed for “hackability” and “remixability,” Web 2.0 places us squarely in the middle of a very grey space. Sample 1: Web Based Email Log-In
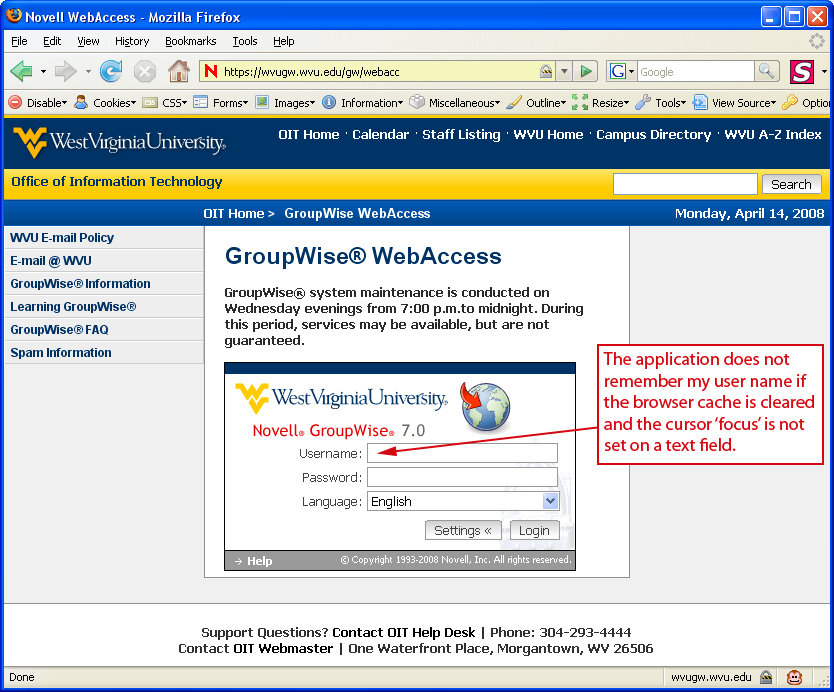
Given this policy statement, I like to ask my students in classes like technical communication or multimedia writing to consider arguments on whether or not it would be ethical to use Web 2.0 technologies like Web Developer and Greasemonkey to hack the functionality of the login page? The “white hat” position would suggest that hacking copyrighted material of any kind is verboten while the “black hat” position would not hesitate to do so. As I have suggested with this new form of composition, the practice is inevitably grey. I do, as the Red Hat definition of a “grey hat” states, have my own “agenda” for the page. While I am not hacking into an email server, rewriting the functionality of Novell’s interface is certainly not what their policy statement invites. The question of ethics becomes more complex when we consider whether or not I should distribute the script to other frustrated colleagues or even post the script to a site such as userscripts.org. Inevitably, a student suggests that copyright law’s provision for Fair Use should protect our actions were we to be prosecuted and that should put our ethical concerns to rest. However, interpreting what constitutes Fair Use is just as “grey” as our ethical debate. Even if I was to argue for the educational use of the script, it is impossible to predict whether or not this hack would be interpreted as having a negative impact on Novell’s place in the market. Who, after all, could afford to go to court to defend a Fair Use claim? Established research on intertextuality provides the encouragement to move ahead with writing the script – not Fair Use. Likewise, recent publications such as George Pullman’s (2005) “From Wordsmith to Object-Oriented Composer” and Bill Hart-Davidson’s (2005) “Shaping Texts That Transform: Toward a Rhetoric of Objects, Relationships, and Views,” which have included detailed code and addressed object-oriented programming and its relationship to writing, have encouraged me to include code in this text. Pullman’s and Hart-Davidson’s publications contain explications for lines of XML as well as HTML forms and the use of more challenging Perl and CGI scripts. As Pullman remarks, “Believe me, if I can do this kind of thing, anybody can” (p. 57). I am including the code for my Greasemonkey scripts below because I feel the same way about using these new Web 2.0 technologies. Although mastering Web Developer, Greasemonkey, or computer languages like JavaScript are not required to introduce students to white, black, and grey hat ethics, we should not shy away from engaging these new technologies. Below in Figure 1 is a screen shot of the login page for my university’s web-based email:
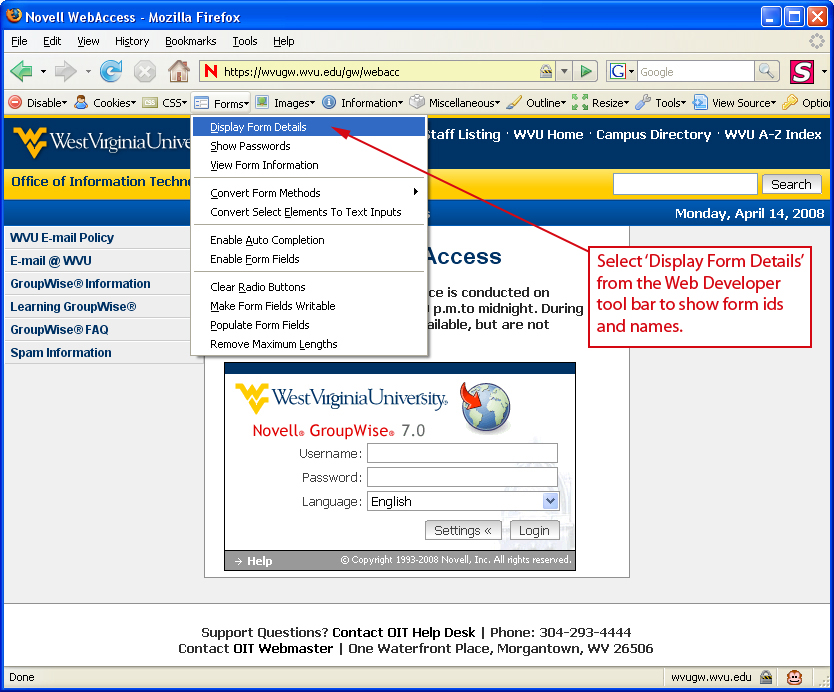
Using Web Developer’s tool bar, a user would click “Forms” and select the first menu item “Display Form Details” as shown in Figure 2.
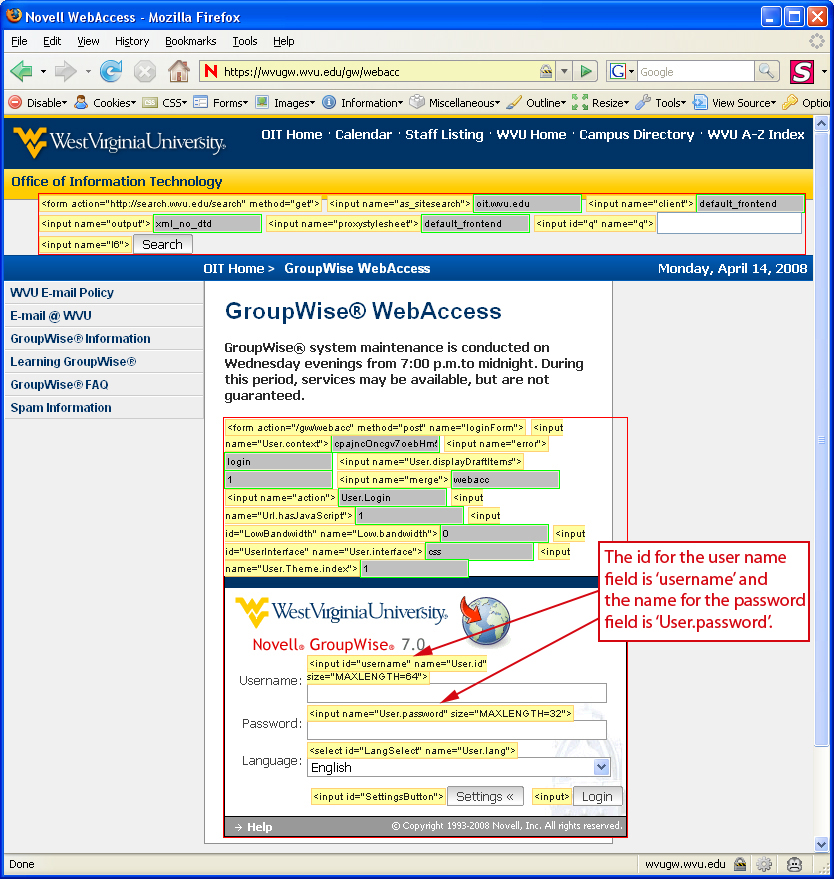
The results from selecting “Display Form Details” are shown below in Figure 3.
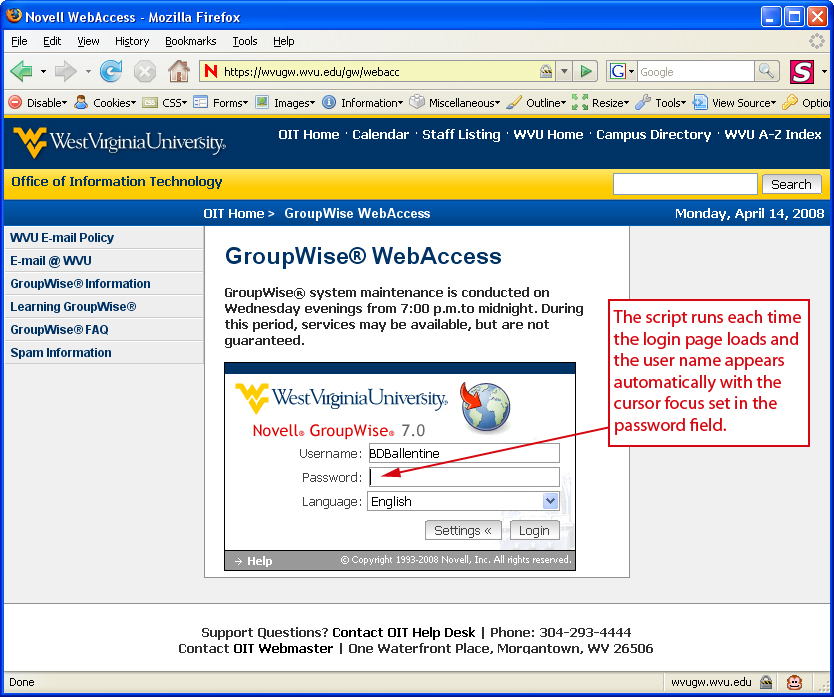
The Web Developer extension displays information on any of the HTML forms on the page, including the search function at the top of the screen. To write the hack, we need information on the text fields for the user name and password. Web Developer shows us that the “id” for the user name is simply “username” but that the password field does not have an id. We use the field’s “name” to manipulate the page and that value is “User.password,” this is enough information to begin writing our Greasemonkey script. Scripts can be composed with any word processing application or HTML editor. The only stipulation requires the file saved with the “user.js” suffix. The word “user” makes the file recognizable as a Greasemonkey script and the “js” stands for JavaScript. My filename is “GW-autocomplete.user.js” in this example. In order to install the script, Greasemonkey must first be downloaded and installed. Afterwards, I simply click on the “user.js” file to load the script. This script automatically loads when I next visit the login page for my university email. The code is centered on one basic JavaScript function that contains two variables. The first variable that I named “login” is used to automatically assign a value to the user name field in the form. I can do this because I used Web Developer to discover the “id” of the field which is “username.” With the script, I declare the value of “username” as my own user name or “BDBallentine.” The second variable I named “setit”. Again, we know from Web Developer that the “name” for the password field is “User.password”. All I wish to do is make or “set” the cursor flashing inside of this field so I can type my password and quickly login. This means setting what is known as the “focus” for the cursor on a particular field. Without going into all of the intricacies, the complete script appears as below: // ==UserScript== (function() After the script is installed, each subsequent visit to the web-based email login page yields the desired result as shown below in Figure 4.
Student response to a hack such as this is almost overwhelmingly positive and enthusiastic. Selber’s concept of critical literacy or our opportunity to “engage in micropolitical acts of modification that adapt technologies to users” becomes a modest, but demonstrable reality in the classroom (p. 105). The discussion of ethics is more robust not because we appropriated the framework of white, black, and grey hat hackers, but because students had a hand in or at least were witness to the activity of re-writing the interface. Sample 2: CNN Special Reports
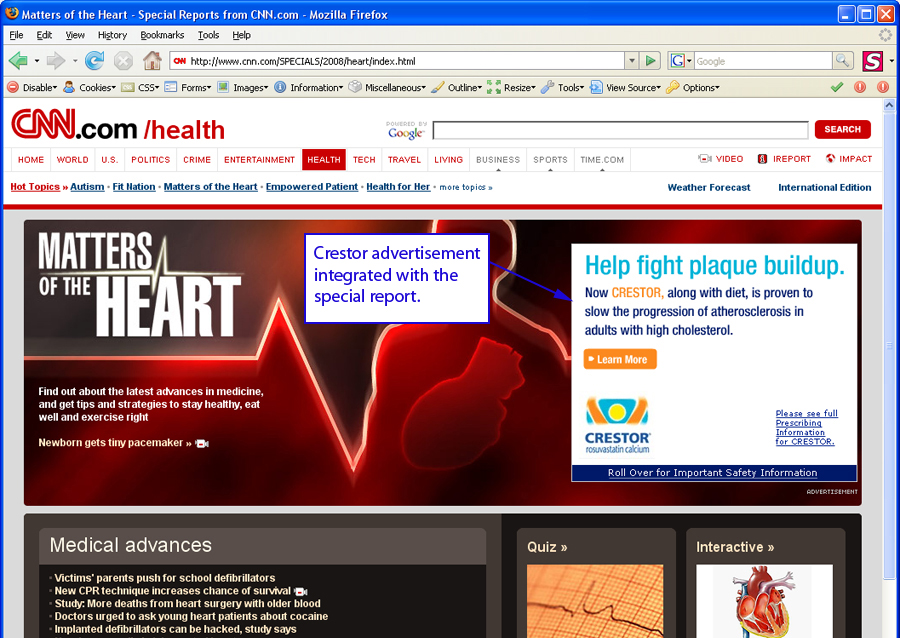
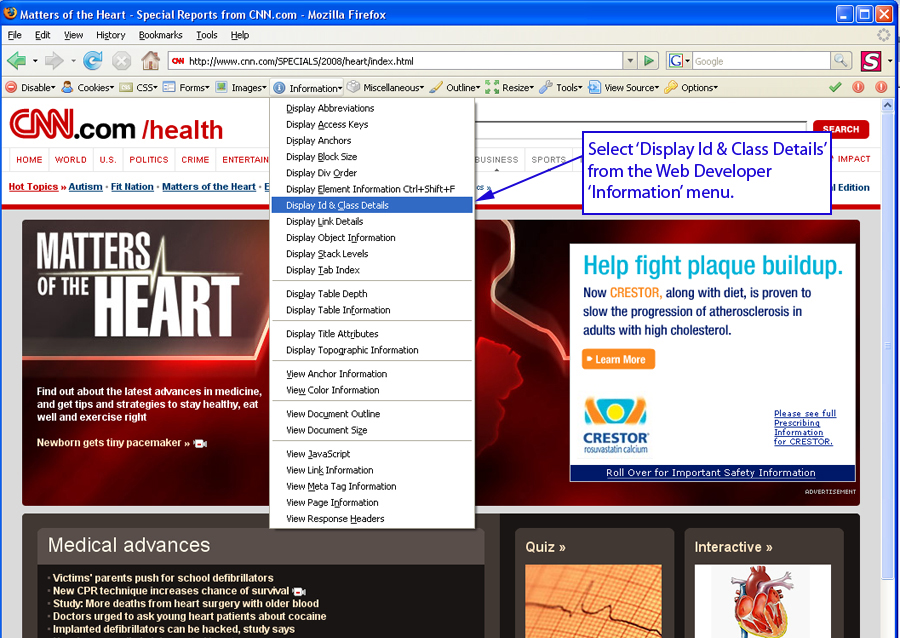
Next, I give the class the option of removing the Crestor advertisement with a Greasemonkey script, though the students often do not agree that the removal is either a purely white or black form of ethical hacking. Our debate over the “grey-ness” of ethically hacking out the advertisement typically leads the class to examine the advertising section of CNN. The students deduce that Crestor has paid for one of the larger and no doubt more expensive advertising placements CNN has to offer (Advertise: Ad Specs & Guidelines, 2008). There is little question that neither CNN nor Crestor would be receptive to the Web 2.0 spirit of openness that invites co-authorship of the special report especially when that co-authorship involves removing expensive advertisements. My students, however, usually decide differently and after their dialog regarding the CNN site they determine that the advertising strategy warrants the “technological reconstitution” of the page (Selber 105). Once again using Web Developer’s tool bar, a user can click on “Information” and select “Display Id & Class Details.”
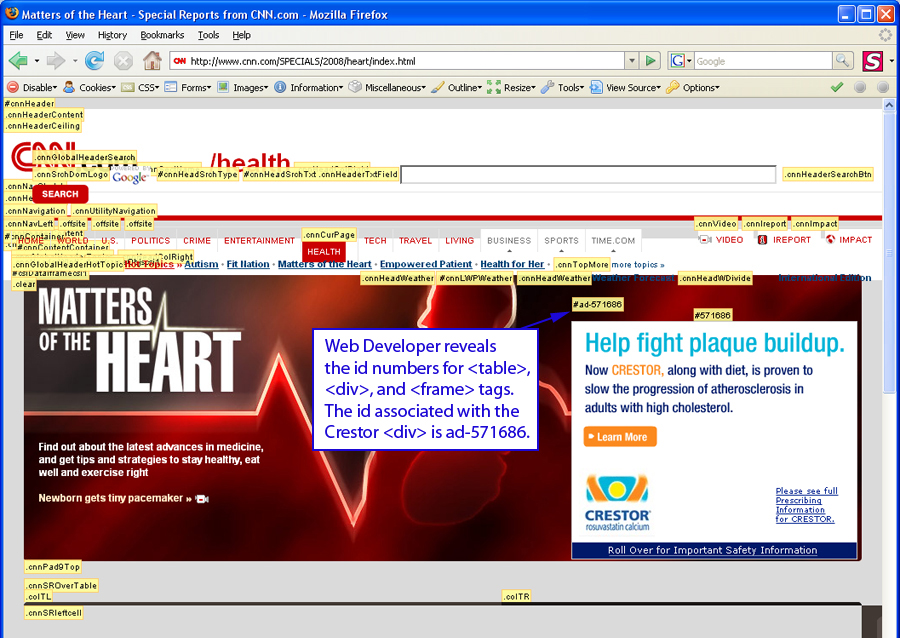
CNN uses a complex structure of <table> and <div> tags to format its pages and Web Developer makes the process of identifying the id associated with the ad easy. The Crestor ad is positioned inside of a <div> tag with the id number “ad-571686” as shown below in Figure 7.
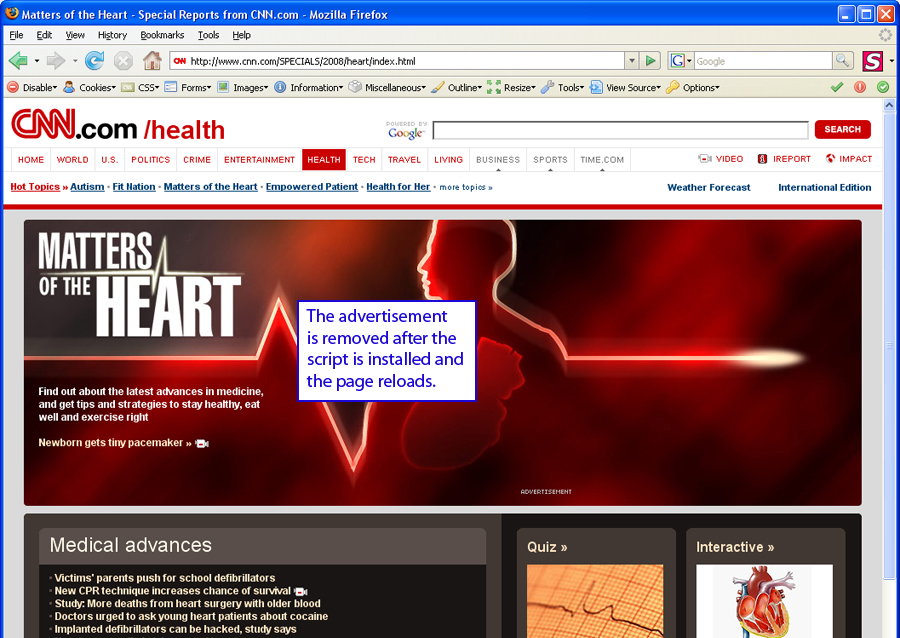
With a few simple lines of code, we compose a Greasemonkey script that hides anything displayed inside of the <div>ad-571686. This script named “CNN-HeartAd.user.js” uses a JavaScript function to dynamically hide the contents of a specific <div> on CNN’s special report. For my part, I created a variable titled “findFrameID” which aligned with the <div> tag’s id. The last step set the “display” of that variable to “none” thus hiding the Crestor ad. // ==UserScript== (function() Readers who have downloaded Greasemonkey can try out this script by installing it and then visiting the CNN special report page on “Matters of the Heart”. Note that if CNN has changed or renamed any of the relevant information the script will cease to function and need to be revised. The final product is below in Figure 8.
According to Raymond, “Every good work of software starts by scratching a developer's personal itch” (Cathedral and the Bazaar, 2008). As these examples illustrate, Web 2.0 empowers users to do just that. These small sample hacks are an effective means to bring students into discussions regarding the ethics of remixing and rewriting an interface. |